Already launched in 24 regions worldwide, the fifth generation of networks (5G), will be the heart of revolutions in industries such as the Internet of Things (IoT). The GSMA estimates the network to hit 1.2 billion connections by 2025. This provides the IoT industry with an array of opportunities for innovation. 5G is not all about faster downloads and upload speeds. It’s a sophisticated technology that provides high-speed connectivity with low latency (below 1 millisecond) and long-distance coverage. 5G is the new dawn of developing technologies such as artificial intelligence(AI), and virtual reality/augmented reality (VR/AR). These are just but a flash of possibilities on what 5G will achieve in the IoT sector. The potential use of 5G is infinite.
But, a flip of the coin of all that functionality and innovation paints a different picture. What does the deployment of IoT in 5G mean when it comes to information security? With a plethora of business opportunities arising in the IoT industry, especially with the number of IoT connected devices projected to increase to 67 million by 2025, many enterprises may find themselves sacrificing their security integrity for dominance in this potential goldmine.
There are several flaws in the 5G architecture which hackers may exploit, including an increase in bandwidth. But, the greatest weak points are IoT devices and their associated enterprises. With the underdeveloped 5G standards and protocols, and the possible overlapping jurisdictions that may exist between IoT and 5G devices, attacks are imminent. The nature of 5G, which combines data, cloud, and IoT also increases security threat levels. Despite the cutting-edge 5G security protocols put in place, one thing is certain. Entering the IoT business space without a solid security plan will end up in an expensive mess.
Let’s look at this example. Back in 2016, there was a Distributed Denial of Service (DDoS). It affected internet service companies including Netflix, Reddit, and Paypal. It also slowed down the operation of the internet. Some experts have claimed that it may have been the greatest in history. What experts found interesting is that the Mirai botnet, which was the source of the attack, is made of IoT. Imagine what damage would have occurred if the botnet would have been deployed on an unprotected 5G network. The destruction would have been unimaginable because of the speed.
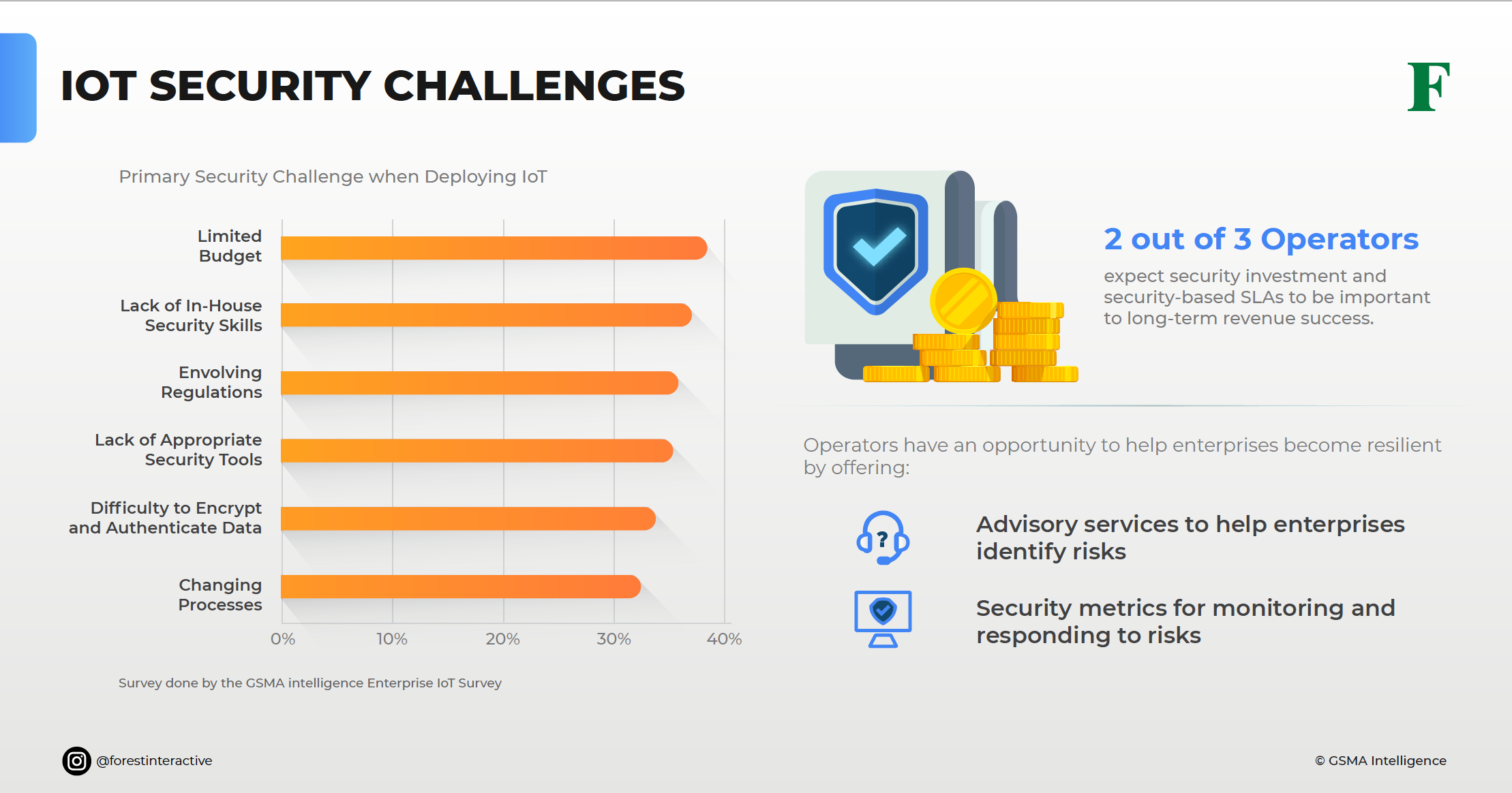
How do IoT firms and other B2B enterprises counter such threats? Given that most of them don’t even have a clue of the risks involved with potential threats if IoT solutions are deployed in the 5G networks. According to the GSMA, the best way to get around threats in IoT and 5G is to get support from operators with experience in managed security services. Mobile operators should help enterprises identify potential threats. They should also provide solutions that will counter cyber attacks.
Equipment vendors also have a part to play in this quest. They should understand that they are also vulnerable to attacks because of the 4G-5G migration process. This is crucial, as enterprises will look up to them for guidance on desired business outcomes.
As for enterprises, the task is simple—act before you pay the price. IBM security released a report that showed a great difference in data breach costs between firms that use cybersecurity automation technologies and those that didn’t. Approximately $2.5 million. Enterprises should also start penetration testing campaigns and constant vulnerability checks. This will play a vital role in reducing the chances of threats penetrating into the 5G infrastructure. Enterprises should also create awareness in their firms. Workers shouldn’t ignore basic security measures. These include using secure logins and passwords and using 2-factor authentication.
 Company Profile
Company Profile Brand Identity Guidelines
Brand Identity Guidelines